Network Access Policy Tool for Verification of Distributed and Layered Security Policy Implementation
Home | People | Screenshots | Documentation | Download | Mailing List
NetAPT has commercialized to become NP-View. The below page is archival. For the latest information, please visit: http://www.network-perception.com
Overview
Access policy implementation misconfiguration of firewalls or other local security mechanisms is a major source of security vulnerability. The complex interactions between distributed and layered policy implementation can lead to subtle errors and mask problems.
The Network Access Policy Tool performs a comprehensive security policy analysis to identify the deviation of implementation from global access policy.
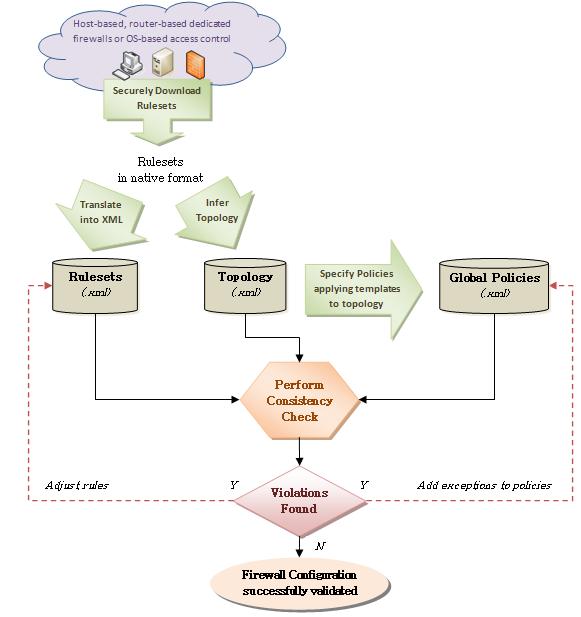
The tool can be run online (connected to the devices subnet) or offline (reading input information from files). It takes as input (all in XML format):
- a network topology (drawn and specified using the tool user interface or inferred from the rulesets)
- the rules implemented by the security devices in that network (either read from a file or automatically collected via remote access and converted to XML if the device is on the list of supported devices known by the tool).
- the global access constraints that the user wishes to enforce on that network (either read from a file or specified using the tool user interface).
This information is used to automatically establish a model of multiple layers of security policy (i.e. firewall at network layer and application layer security protocols) and perform choice between two kinds of analysis of this model:
- an Exhaustive analysis to identify specific flaws in the policy implementation that may cause a violation of the global access constraints. When used in online mode, the tool can optimize the analysis for localization and can perform incremental exploration of the model to support analysis of local changes in policy implementation.
- a Statistical analysis adequate for larger networks to characterize and quantify the conformance of the policy to the global access constraints. This kind of analysis uses importance sampling techniques to support a variety of metrics, backed by appropriate mathematical constructs, special data structures, as well as analytical (and if that is not possible, empirical) proofs of variance reduction.
Both kinds of analysis are provided in XML format and viewed in the tool user interface for easier display (i.e. highlighting of misconfigured devices, violation details, etc.).
The Tool
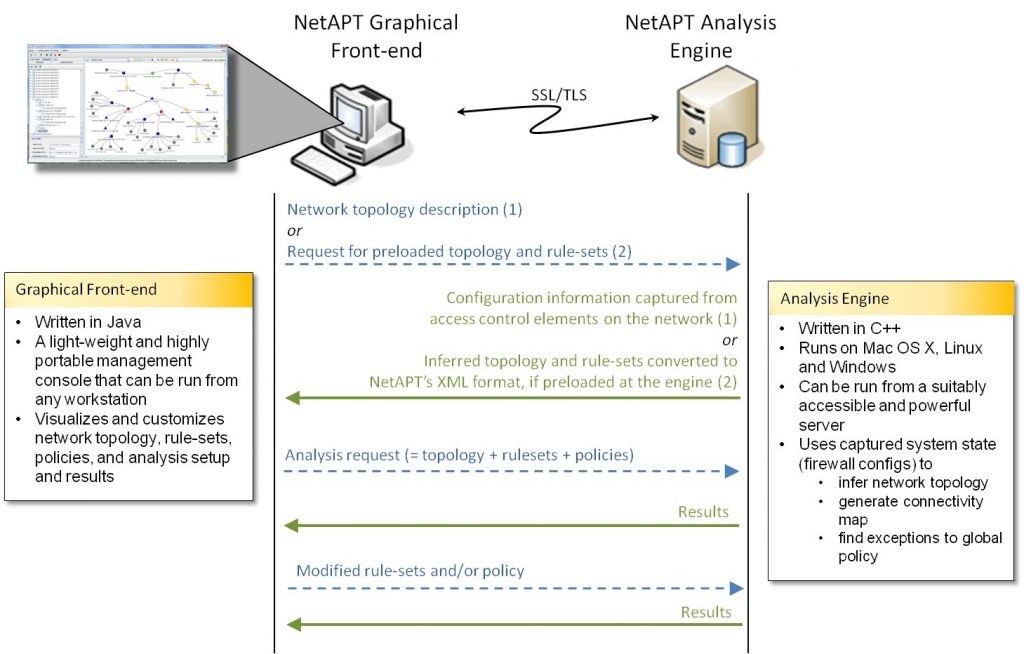
The tool has two components:
- Analysis Engine (or NetAPT Appliance)
The NetAPT Appliance is a black box machine that can be plugged into a suitable sub-network, such that it has access routes to the various security enforcement mechanisms/devices and automatically gather the relevant configuration information. The appliance can also be run standalone with the topology, rulesets and constraints formatted and readable from a file. The engine has been written in C++. - User Interface (GUI or management console)
The GUI can be run on any host that is convenient for the system administrator, provided that it can create TCP connections to the NetAPT Appliance. The use of the GUI is optional but makes easier the specification and display of network topologies, rulesets, policy constraints and analysis results. The GUI has been written in Java Swing.
People
Faculty
Staff
Students
- Sankalp Singh
- Rakesh Kumar
- Zach Yordy
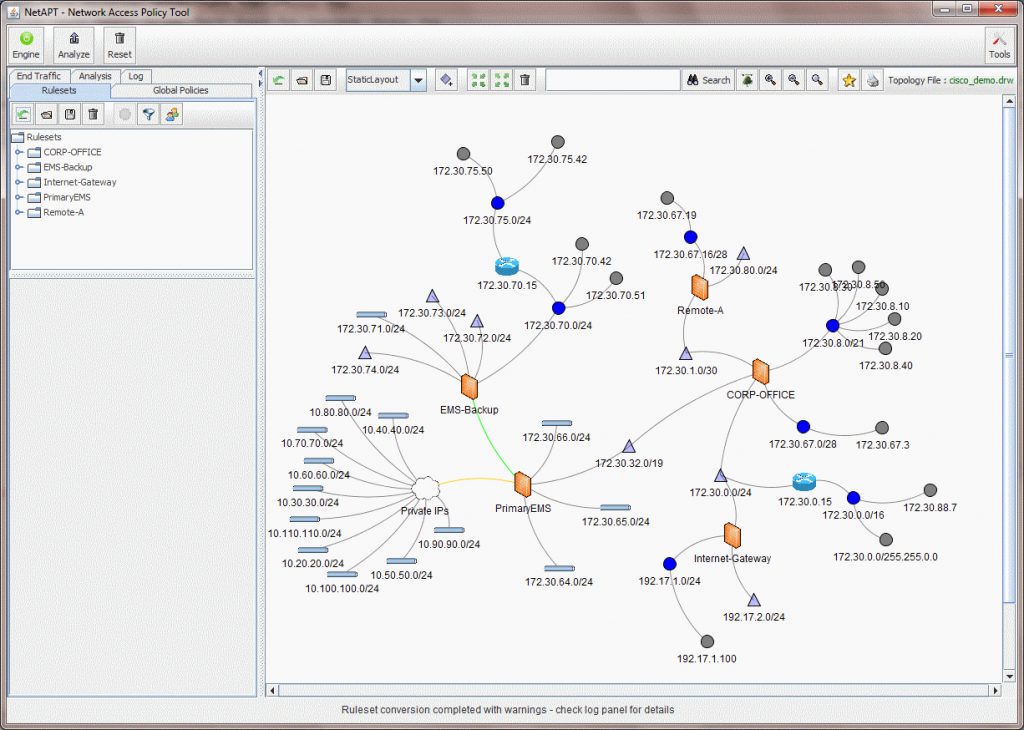
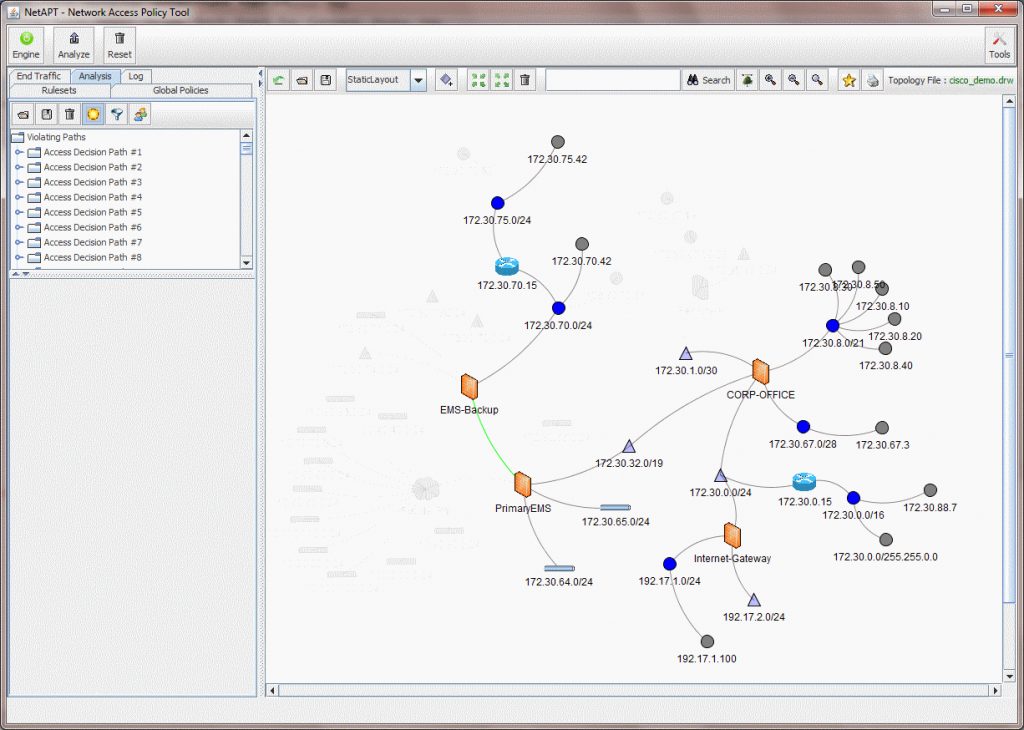
Screenshots

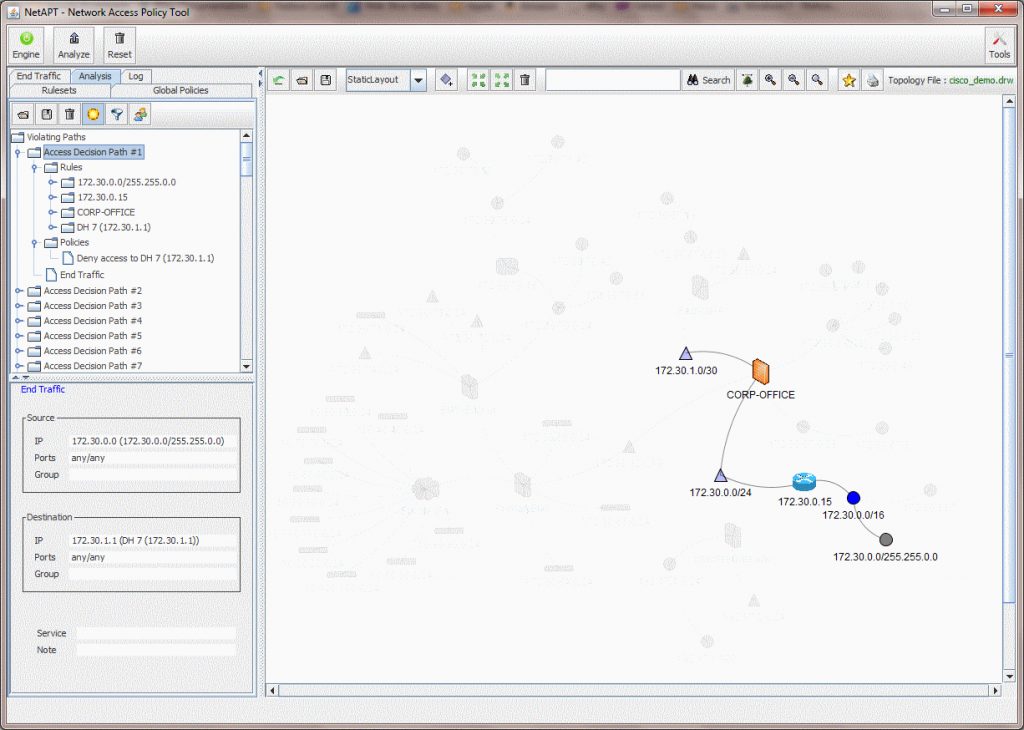
Documentation
Use cases
An overview of the main benefits brought by NetAPT for different stakeholders:
Documentation
Accessing the documentation requires the credentials that were sent when you received a download link for NetAPT. If you lost those credentials, please contact us.
- Installation guide for Windows (PDF)
- Installation guide for Mac (PDF)
- User Manual for NetAPT (PDF)
- Cheat sheet (PDF)
If you encountered a problem using NetAPT, please email us a Problem Report Form at netapt-users@iti.illinois.edu.
Download
NetAPT binaries for Windows and Mac OS are currently available with an evaluation license. Send an email to info@network-perception.com to request a copy of the tool and we will follow up with you..
Contact: User Mailing List
NetAPT mailing lists have been disabled. To receive updates on the tool or to exchange information with other users, please contact us as info@network-perception.com.
Site Last Updated On: 02/27/2013